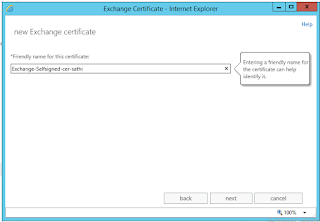
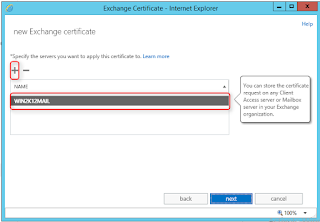
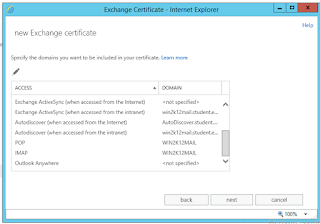
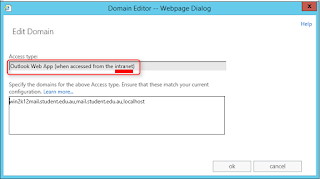
Multi Tenant Email Server Configuration
In this tutorial I am going to explain how to host multiple email domains on one Domain controller and Exchange server.
Say for example , A company have two Branches and they are namely Dandenong and Mulgrave. The company doesn't want to have common email address. They want to have emails specifically branches
So the users in Dandenong will have their mail address as user@dande.mks.com.au and the user in Mulgrave will have user@mul.mks.com.au. We can do the same to even different domains , Lets see how we can do this...
First of all to do this we need to have UPN ( user principle names ) and OU ( organizational units ) to create emails and user account. Lets see how we can do this
Create OUs
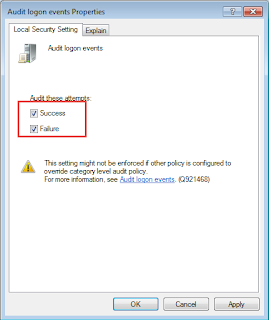
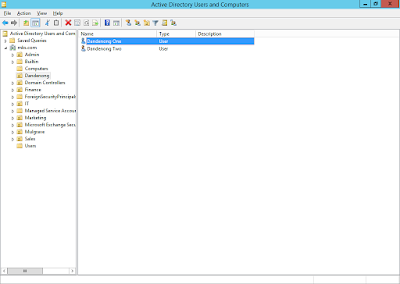
1. . Navigated to
‘Active Directory Users and Computers’ and created OUs for Dandenong and
Mulgrave:
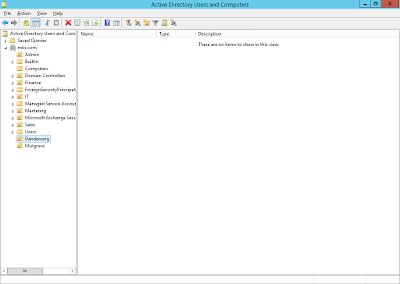
2. Created two users in each OU,
Mulgrave One and Two for the Mulgrave OU, and Dandenong One and Two for the
Dandenong OU:
Create UPNs:
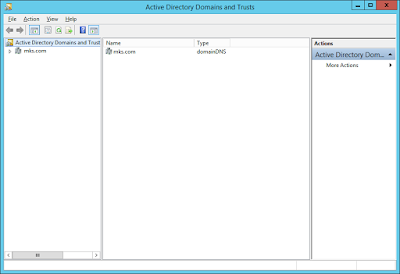
Navigated
to ‘Active Directory Domains and Trusts’:
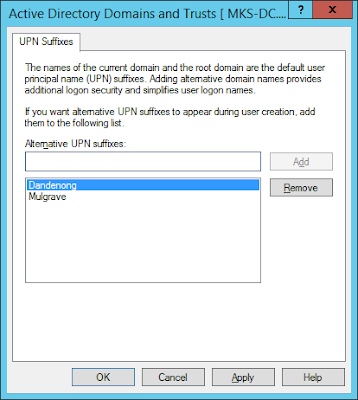
Right-clicked ‘Active Directory
Domains and Trusts’ and selected ‘Properties’. Added ‘mulgrave.mks.com’ and ‘dandenong.mks.com’
as alternate UPN suffixes and clicked ‘Apply’ and ‘OK’:
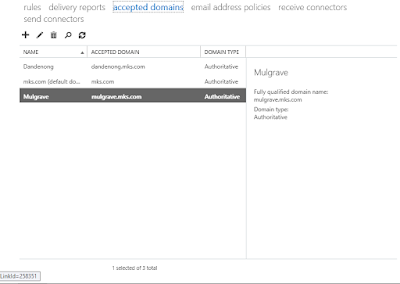
On the Exchange server :
Navigated to ‘Accepted Domains’ and added the ‘dandenong.mks.com’ and 'Mulgrave.mks.com' UPN as
an accepted domain on the Exchange server:
Create Email Policy
Navigated to the Exchange
Administration Centre, and went to ‘Mail Flow > Email Address Policies’:
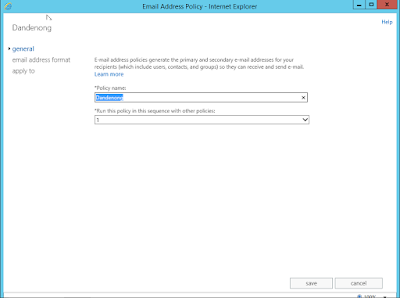
Under
‘Email Address Format’, changed the address format to ‘dandenong.mks.com’
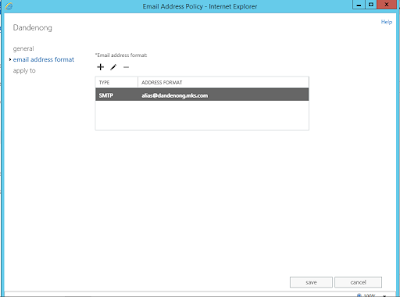
Under
‘Apply to’, added a new rule and selected ‘Recipient Container’. Selected the
previously created ‘Dandenong’ OU and clicked ‘Save’
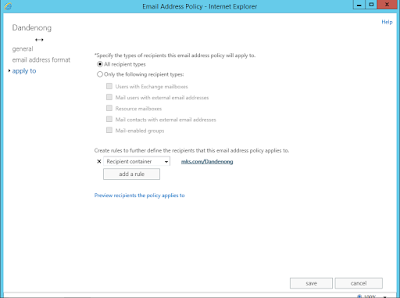
Created a new email policy named
‘Mulgrave’ and repeated Steps for the ‘Mulgrave’ OU:
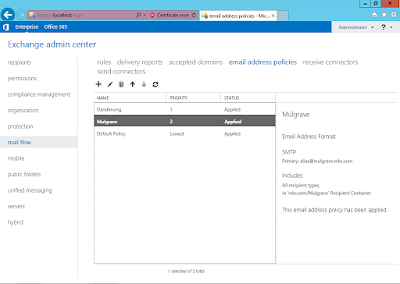
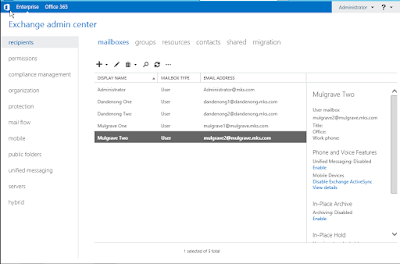
Created Users Email
Navigated to ‘Recipients’ on the
Exchange Admin Centre and added the Dandenong One, Dandenong Two, Mulgrave One
and Mulgrave Two users from the OUs previous created: