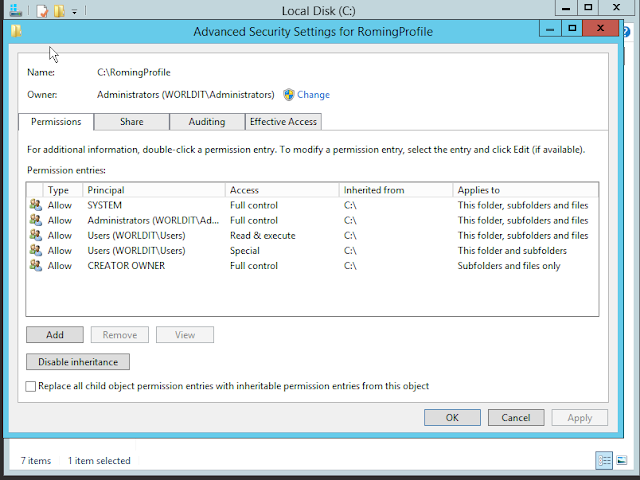
IPv4 SUBNETTING
Given network Address 192.168.1.0/24, you have been asked to
use the given network address to do the subneting and configure the network.
Step 1: Always you need to start with the Highest IP
requirement, so the highest IP requirement is 30.
Calculating network address of each network from the given
classful lP address is called VLSM.
To find the classless IP network we have to first find the
required host bits.
2n -2 ³REQUIRED
IP ( n is number of host
bits)
2n -2 ³30
2n ³30+2
2n ³32
2n ³25
n=5
so required number of host bits = 5
that’s bring the subnet mask bits to à 32-5=27
so the network address of first network is 192.168.1.0/27
Since the network address is 192.168.1.0/27 , we should be
able to find the first and last IP address in this network.
To find the first IP address, we need to convert the IP
address to binary format and change all the host bits to zero (0)
192.168.1.0
11000000.10101000.00000001.00000000 (Binary format) in this
first 27 bits are assigned to network and the last 5 bits assigned to Host.
11000000.10101000.00000001.000|00000,
we could see all the host bits are zero so this is the first IP address in this
network, but this is also the network address. There for we cannot use this
address to any end device, this address is used to identify the Network
Network Address = 192.168.1.0/27
Now we need to find the last IP address,
To find the last IP address change all the host bits to one
(1)
11000000.10101000.00000001.000|00000
change the host bits to one
11000000.10101000.00000001.000|11111
when you convert this to Decimal we will get the Last IP address which is
called broadcast address.
11000000 = 192
10101000= 168
00000001= 1
000|11111 = 31
So, the Broadcast IP address is 192.168.1.31/27
So we can conclude this as follows, for 30 IP address
requirement, we need /27 network
Which has a range from 192.168.1.0/27 --- 192.168.1.31/27
______________________________________________________________________________________________________________________________________________________
Now we need to calculate for the second biggest network
2n -2 ³REQUIRED
IP ( n is number of host
bits)
2n -2 ³15
2n ³15+2
2n ³17
since its greater than or equal we can change this to closest 2 to the power
number which is 32 (1,2,4,8,16,32,64,128,256)
2n ³32
2n ³25
n=5
so, required number of host bits = 5
that’s bring the subnet mask bits to à 32-5=27
so the network address of the second network is
we have used up to 31 , that’s mean we can start the next
network from 32.
Network address is : 192.168.1.32/27
Now we need to find the last IP on this network, to do the
calculation we will again convert this Network address to Binary
11000000.10101000.00000001.00100000
Last IP address has all the hosts bits set to one
11000000.10101000.00000001.001| 11111
which is 192.168.1.63 /27 in binary
so the range of the second network is 192.168.1.32/27 ---
192.168.1.63/27
______________________________________________________________________________________________________________________________________________________
Now we can calculate the third network which has a
requirement of 8 IP address
2n -2 ³REQUIRED
IP ( n is number of host
bits)
2n -2 ³8
2n ³8+2
2n ³10 since its greater than or equal we can change
this to closest 2 to the power number which is 16 (1,2,4,8,16,32,64,128,256)
2n ³16
2n ³24
n=4
so, required number of host bits = 4
that’s bring the subnet mask bits to à 32-4=28
so, the network address of the second network is
we have used up to 63, that’s mean we can start the next
network from 64.
Network address is: 192.168.1.64/28
Now we need to find the last IP on this network, to do the
calculation we will again convert this Network address to Binary
11000000.10101000.00000001.0100|0000
Last IP address has all the hosts bits set to one
11000000.10101000.00000001.0100|1111
which is 192.168.1.79 /28 in binary
so the range of the second network is 192.168.1.64/28 ---
192.168.1.79/28
______________________________________________________________________________________________________________________________________________________
-->
similar way we need to calculate to N12,N23,N13, but in this
network we need only 2 IP address.